We utilize the Microsoft ESAE/Red Forest in my production environment for our Active Directory security hardening. What is this? Well, it’s the path of least privilege in Active Directory. According to this Microsoft article, the underlying principles can be achieved in as few as 3 concepts summarized below:
Phase 1 of the roadmap is focused on quickly mitigating the most frequently used attack techniques of credential theft and abuse. Phase 1 is designed to be implemented in approximately 30 days and is depicted in this diagram:
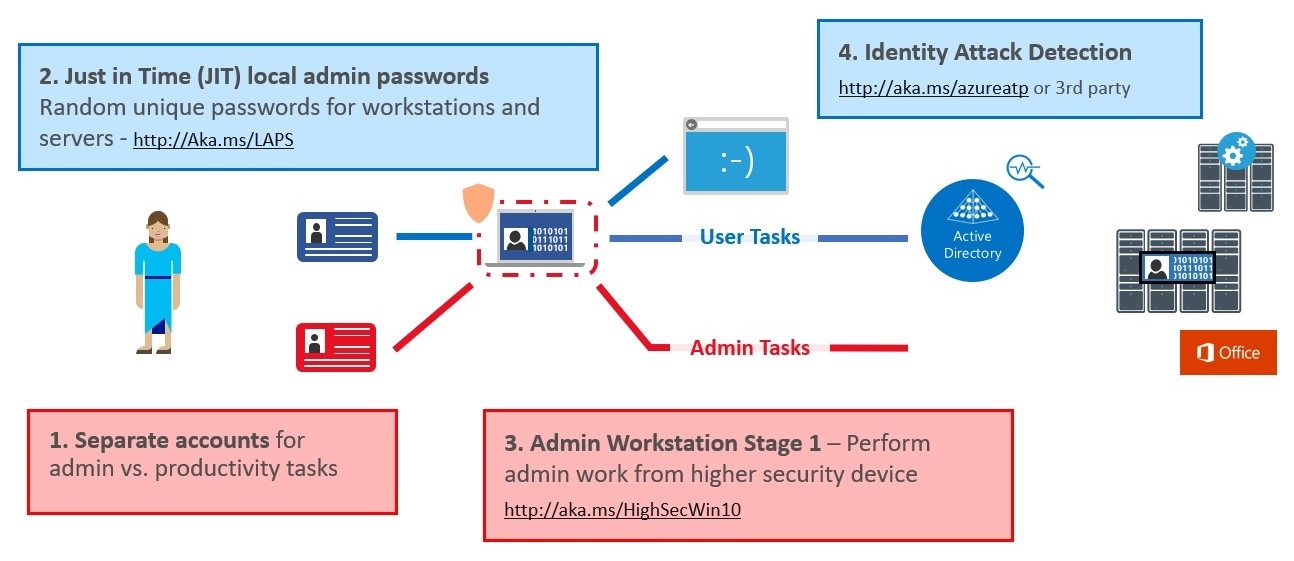
The biggest takeaway here is that you should be using separate accounts for administrator work vs a single account with Domain/Enterprise/whatever level admin membership… For real, do this NOW!
Phase 2 builds on the work done in phase 1 and is designed to be completed in approximately 90 days. The steps of this stage are depicted in this diagram:
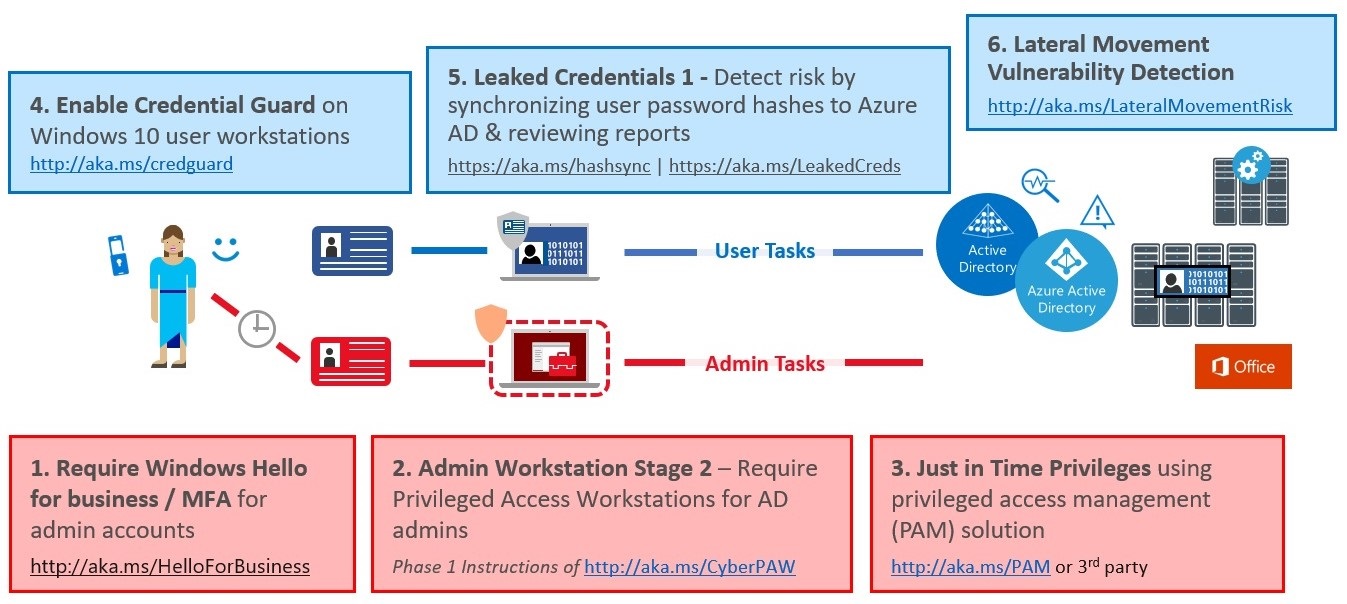
Here, the number one priority should be MFA and Azure Credential Guard. MFA saves lives in my book.
Phase 3 of the roadmap builds on the steps taken in Phases 1 and 2 to strengthen your security posture. Phase 3 is depicted visually in this diagram:
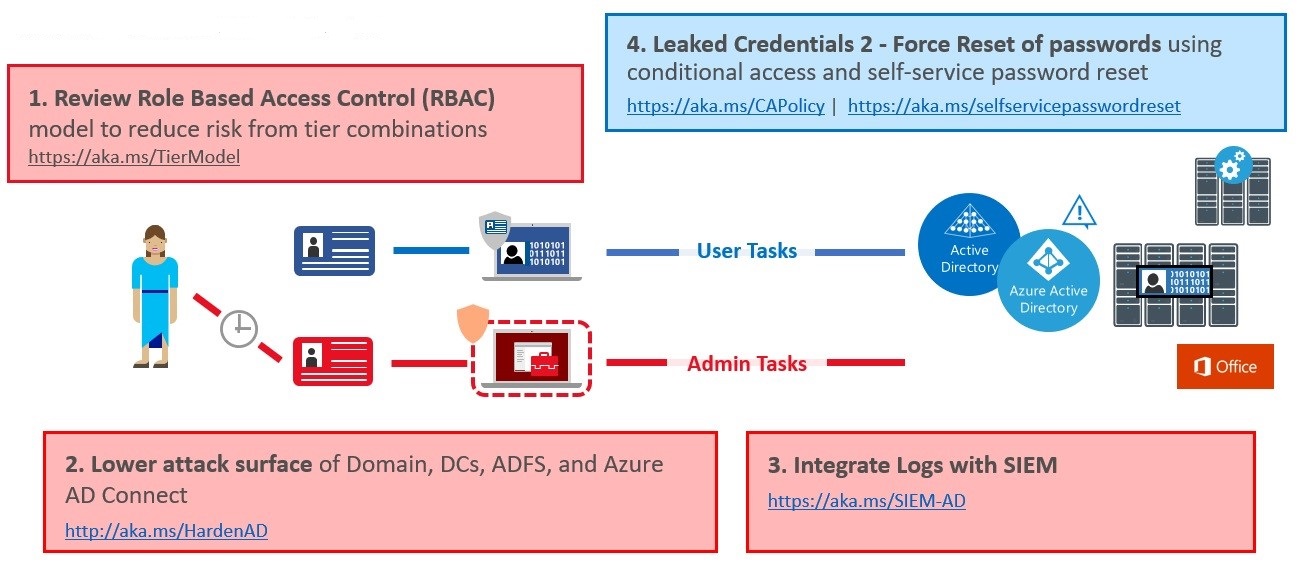
Finally, the biggest piece here is the threat surface reduction. I’d even go further and reduce the total number of Domain Controllers (DC) in satellite data centers unless operationally prudent and only run the Windows Server Core OS variety personally. But, if your PowerShell-fu isn’t there or you don’t feel comfortable with it or RSAT, then at least don’t use your DC for ANYTHING else. The amount of times I’ve seen DC’s running Line of Business software or any number of other roles including IIS. Yikes.
My adjusted phases
Far be it from me to question the architects of AD, but I do have a few suggestions/inputs/consolidations I’d suggest… Primarily, condense phase 1 and 2, focus more on monitoring with Azure Event Hubs for your own SIEM/Azure Sentinel and ATP/Other threat detection platform. After all, active monitoring for anomalies is the best course of action. Follow this up with Azure B2C and you have a tight ship!